About the Client
Basik (client) was looking to scale up their games from a few thousand user-base to millions of users and have approached Expert Cloud Consulting (ECC) aka GPUonCLOUD for the same.ECC team worked with Basik and designed & deployed the AWS EKS Solution including DevOps for all microservices
Problem Statement
Basik team approached us to migrate their on-prem setup having k3s setup to AWS Cloud. The ask was to have a Scalable setup as they were expecting increase in demand and highly available setup to ensure uptime along with fully automated CI/CD pipelines.At customer’s On-Prem setup they felt their security posture for infra is not appropriate as they could not monitor individual user activity, have a secured way to connect to servers.It was also observed that the maintenance activities often led to an extended downtime than expected.Customer were also concerned about securing their servers as per the best practices and monitor non compliance by automating it in some way.
Proposed Solution & Architecture
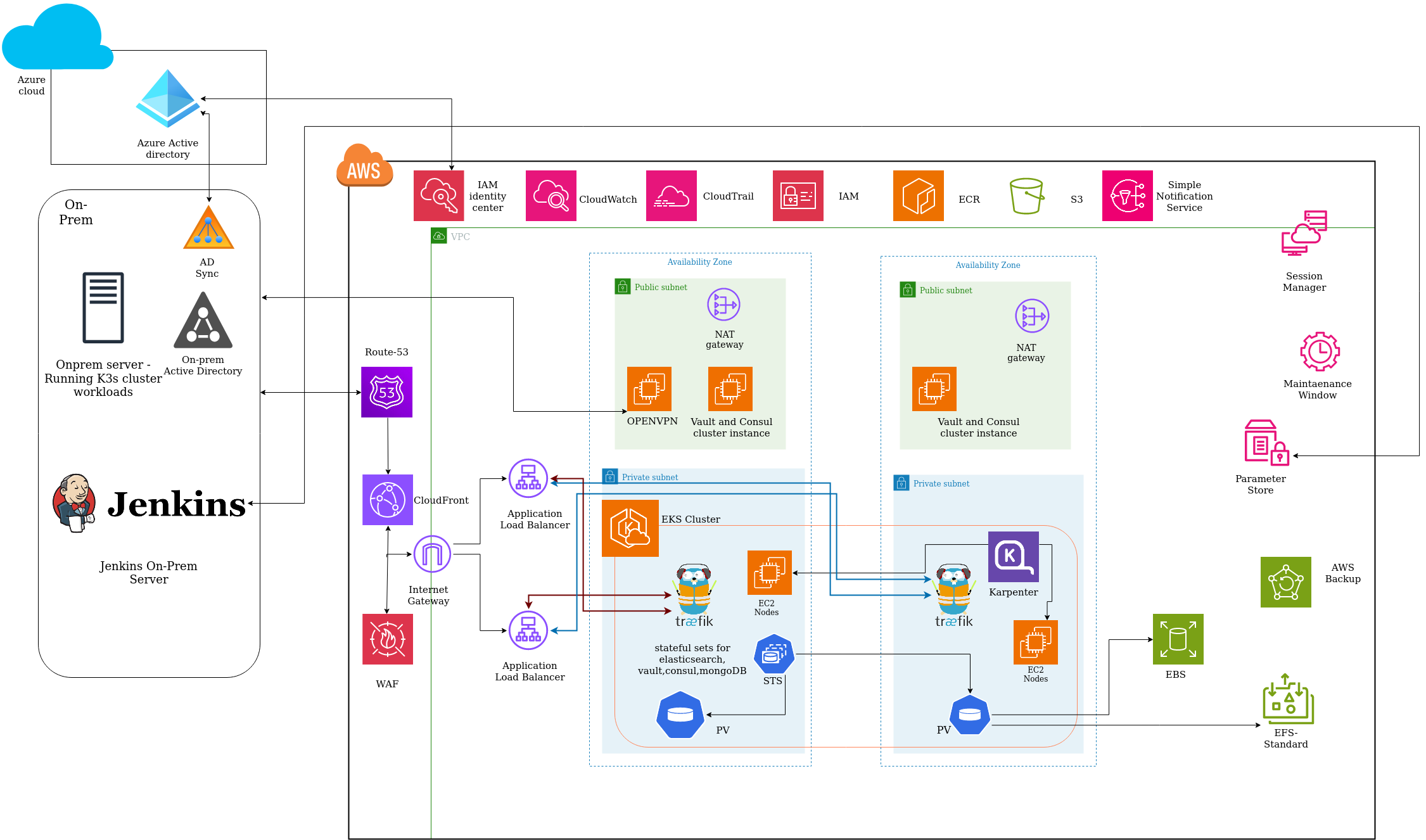
Post analysis of the on-prem setup our team did the required design and provisioning of the below AWS Components in Mumbai region-
- -AWS EKS with worknodes across multi-AZ for HA,
- -AWS SSM for Instance Connect to EC2 connecting to non-standard SSH port, traceability of the logs in CloudTrail, and Instance tagging,
- -Karpenter for Scalability of the microservices,
- -Jenkins for CICD, ECR, IAM roles for ECR, and Github integration for fully automated pipelines
- -Deployement of entire cloud infra with Terraform, Ansible, Packer - IaC and version controlled code
- -EFS & EBS Volumes for Storage and associated provisioners - for persistent data in kubernetes statefulsets
- -OpenVPN Configuration and Connectivity to on-prem nodes for Secured connection to the cloud resources
- -Hashicorp Vault Cluster deployments in EC2 with AWS SSM for node discovery basis tags for handling applications secrets
- -Traefik API
- - Prometheus, Grafana and EFK for traceability and observability along with CloudWatch, CloudTrail etc
- Additionally, the proposed solution addresses below with the help of AWS SSM components- For providing a safe way to connect to servers it was suggested to use AWS SSM SessionManager to have console and CLI access without exposing open ports and logging of the same.
We proposed customer to leverage AWS SSM RUN for server patching of their core Infra servers ,eg OpenVPN, Vault,Consul clusters etc. Thereby reducing the downtime required in scheduled maintenance.
Outcomes of Project & Success Metrics -
Below are the highlights of the Solution Provided -
- Highly Scalable Solution
- Highly Available Infra Setup across 2-AZ’s
- Successful migration of multiple microservices
- Version controls of the Infra as Code leveraging Terraform
- Resilient, easy to replicate environments using IaC and Solutions with recent well-known components such as Karpenter, Traefik, Hashicorp Vault/Consul, MongoDB, Redis etc clusters
w.r.t. AWS SSM the outcomes are as below -
- Standardized processes for secured access.
- Automated patching and quick recoverability within maintenance window.
- security posture notifications on daily basis for compliance and necessary actions.