Introduction
DevOps has established itself as the foundation for effective software development and deployment in today's fast-paced digital environment. DevOps pipelines speed up the process of producing high-caliber apps, but they also present security concerns that need to be dealt with before they arise. We'll look at how to strengthen your DevOps pipelines with cutting-edge security techniques in this blog post to make sure that your software is not only supplied promptly but also protected from potential risks.
Organizations are now able to deploy software more quickly and frequently because of DevOps principles, which have altered the software development lifecycle. However, if security is not included in the process, this enhanced speed could unintentionally reveal vulnerabilities. DevOps security is crucial for the following reasons, which are all very important:
DevOps pipelines: are designed to quickly deploy new features and updates. However, this speed makes it possible for security weaknesses to spread. Incorporating security measures is essential to preventing vulnerabilities from being used in production.
Constant Changes: CI/CD pipelines, which stand for continuous integration and continuous deployment, frequently entail code updates. Every shift presents the potential for new security concerns. You can identify and reduce these dangers with the use of advanced security procedures.
Regulatory Compliance: Strict regulatory regulations, such as GDPR, HIPAA, or PCI DSS, are applicable to many businesses. Your DevOps approach may not be compliant, which could result in severe fines.
Protection of Reputation: Security lapses can damage the standing of your company. Modern security procedures maintain the integrity of your brand while also protecting your software.
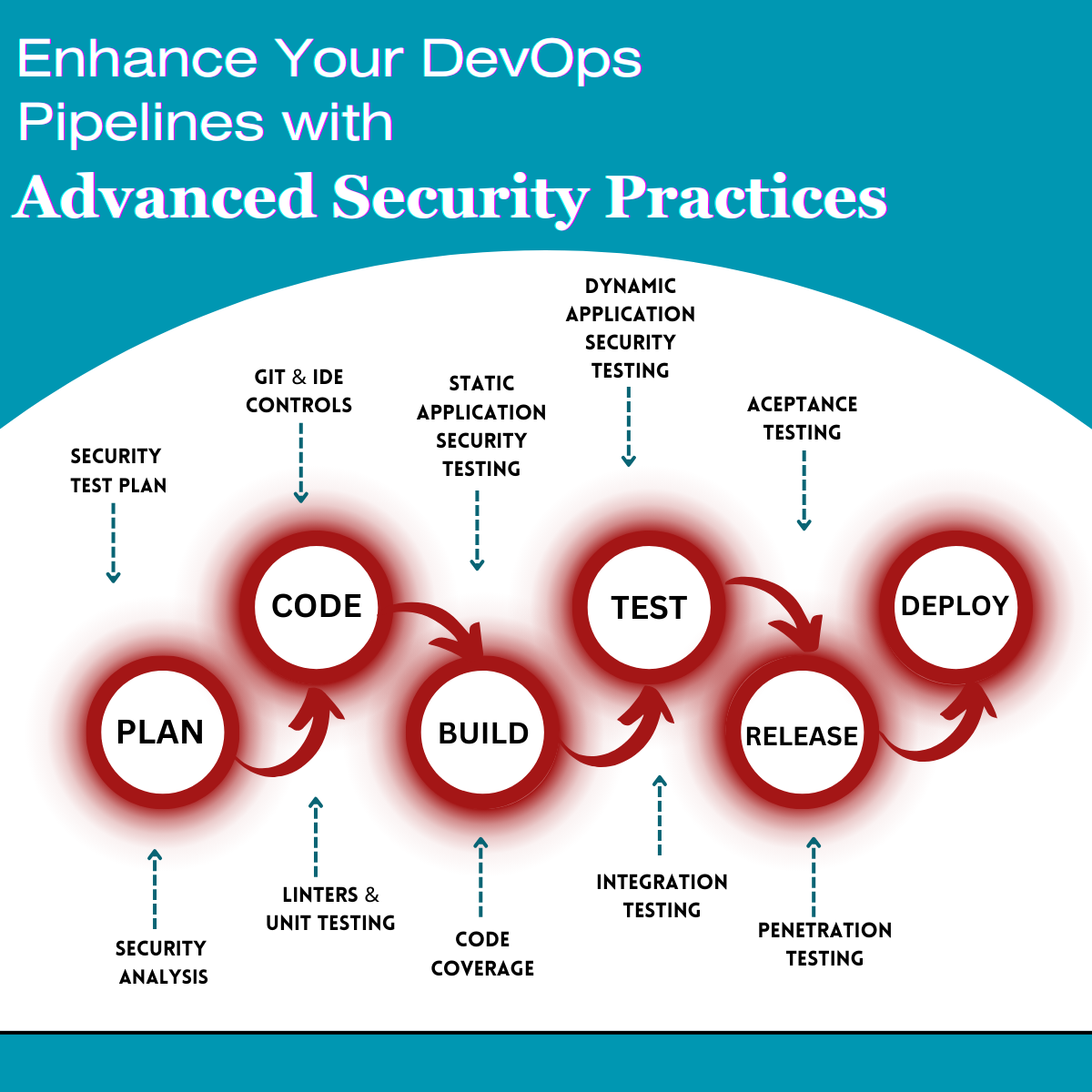
Enhancing Your DevOps Pipelines with Advanced Security Practices
Let's now explore some cutting-edge security techniques that can strengthen your DevOps pipelines:
Integrate automated security testing: instruments into your CI/CD pipeline. Your code can be scanned for vulnerabilities using programs like OWASP ZAP, Nessus, or SonarQube, guaranteeing that no serious problems elude detection.
Container Security: If you use containers, you might want to use Kubernetes Pod Security Policies or Docker Security Scanning as container security measures. You may identify and reduce security threats in your containerized apps with the aid of these tools.
Security for Infrastructure as Code (IaC): When defining and managing your infrastructure, adopt IaC principles. Using best practices, tools like Terraform and AWS CloudFormation may be secured to make sure your infrastructure is resistant to threats.
Secret Management: Use reliable secret management tools like HashiCorp Vault or AWS Secrets Manager to protect sensitive data, including API keys and passwords. Make sure that your codebase never contains any hardcoded secrets.
Shift Left Security: Shift Left security is implementing security as early as practicable in the development process. To lessen the chance of vulnerabilities, developers should obtain security training and use secure coding techniques from the beginning.
Conclusion
In today's threat environment, adding advanced security measures to your DevOps pipelines is a need, not an option. Security lapses can cost a lot of money, cause compliance problems, and harm reputations. You can defend your DevOps pipelines against potential attacks by automating security testing, securing containers and infrastructure, maintaining secrets well, and implementing Shift Left security principles. Keep in mind that your DevOps culture should incorporate security to make sure that your software is not only quick but also durable and secure. Keep up with the times and safeguard your company's digital assets with cutting-edge DevOps security procedures.